A Few months ago, I wrote a blogpost about blocking legacy authentication on your tenant. The advise was to block these protocols and start using Modern Authentication right away. Days have passed and basic authentication protocols are still used, way to often. Meanwhile, Microsoft has provided us some updates about the deprication of the protocols.
Since my first post, I got a lot of questions about it. That’s why I decided to write an update on it – including all information you should know about.
Basic Authentication Protocols
Legacy Authentication refers to all protocols that use Basic Authentication. Basic Authentication only requires one method of authentication (password) and isn’t even compatibel with multi-factor authentication. That’s why enabling multi-factor authentication isn’t effective if you don’t block legacy protocols. Besides this, basic authentication clients are in charge of collecting the user’s credentials and providing them to (any) authority. Modern Verification can only be used with trusted authorities, like Azure Active Directory. The protocols below are considered legacy protocols.
- Authenticated SMTP
- Exchange Online PowerShell
- Exchange Web Services
- IMAP
- MAPI over HTTP
- OAB (Offline Address Book)
- Outlook Anywhere
- Outlook Service
- POP3
- Reporting Web Services
- Other clients
There are protocols that are compatibel with both legacy & modern authentication, like MAPI over HTTP & Exchange Web Services. Microsoft even enabled support for Modern Authentication to POP and IMAP for all Office 365 customers. Of course, your client needs to be compatibel with this (and up-to-date) – and even then you should move to the default connectiviy protocols.
Deprecation of Legacy Authentication
In 2018, Microsoft told everyone that Basic Authentication for EWS would be decommissioned on October 2020. In 2019, they told us that this would be extended to ActiveSync, POP, IMAP and Remote PowerShell. A few updates (and a pandamic) later, these are the facts.
Update 04/02/2021
Microsoft will not disable basic authentication protocols that the tenant is using. At this moment, it’s not clear when this will start.
Microsoft will disable legacy protocols on all new tenants, using Security Defaults. Also, Microsoft will start disabling unused basic authentication protocols on existing tenants. You’ll get a 30 days notice in Message Center.
Microsoft has started enabling Security Defaults on existing tenants, created after October 2019, without Azure AD Premium licenses.
Microsoft will start disabling Basic Authentication for the following protocols in Q2 of 2021 – only if the protocols are not in use!
- Exchange Active Sync
- Exchange Web Services
- POP
- IMAP
- RPS Protocols
- MAPI
- RPC
- Offline Address Book (OAB)
SMTP Authentication will not be deprecated, but will bedisabled for all new Office 365 tenants. If possible, you can re-enable this – but keep in mind this is insecure. If you don’t need it, block it (with the Exchange Authentication policies described below). Also, SMTP Auth will be block on tenants who do not use it.
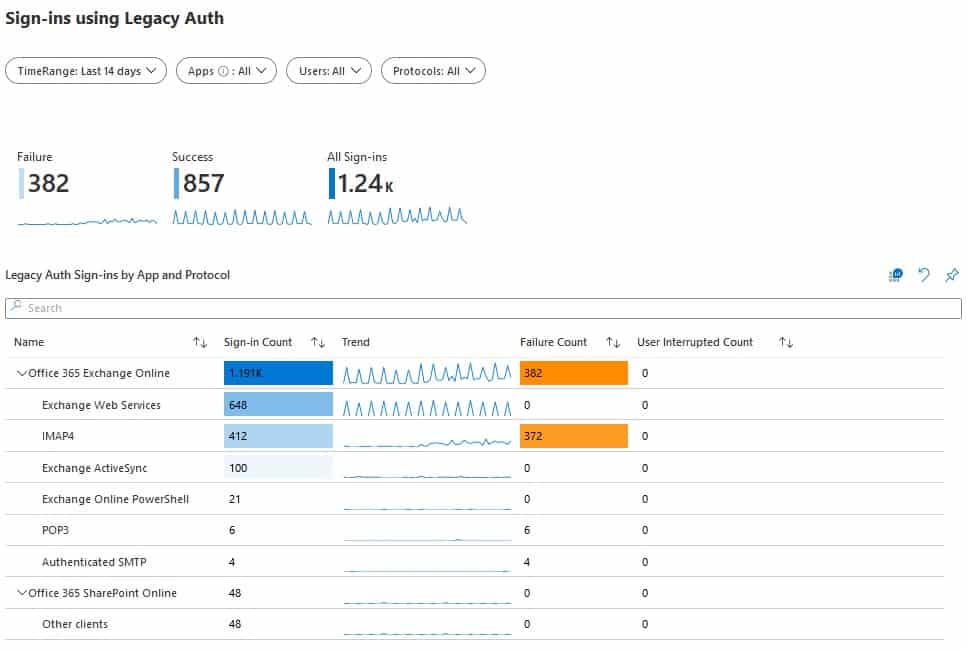
Monitor Legacy Authentication Usage
Microsoft made it very easy to check if your organisation is using legacy authentication protocols. The first method is free, but has only a history of 7 days. For the second method you need an Azure subscription, but it gives you a lot more information.
Azure AD Sign-In Logs
- Navigate to https://portal.azure.com and log on with a user that has sufficient permissions.
Global Administrator, Security Administrator, Security Reader, Global Reader and Report Reader roles can access sign-in logs.
- Open the Azure Active Directory blad and click Sign-Ins. You’ll find this in the Monitor section.
- Add a filter by clicking Add Filters and choose Client App. Click Apply.
- Select all protocols under Legacy Authentication Clients.
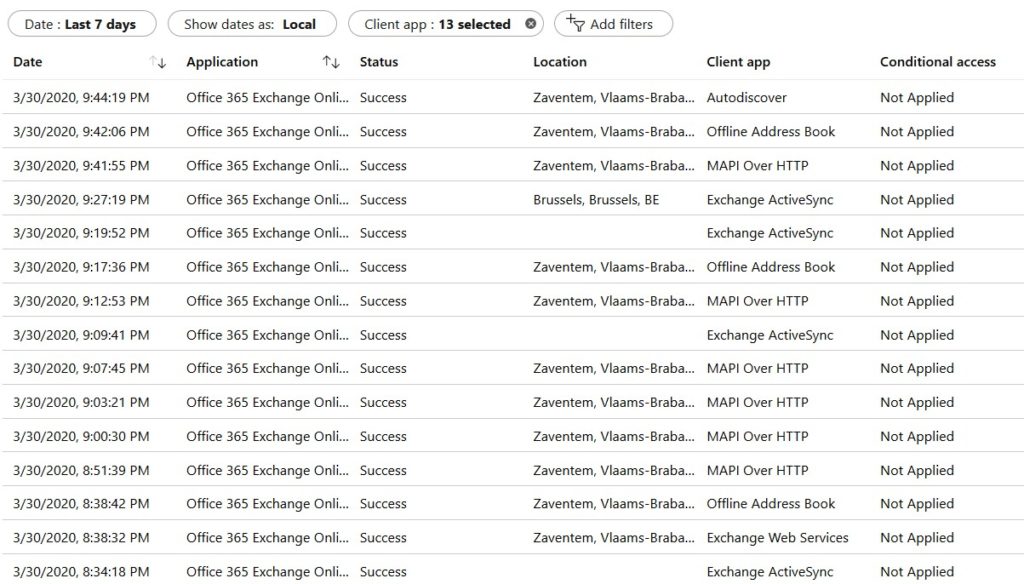
- Analyse all sign-ins or click Download to export the information to JSON/CSV.
Azure AD Diagnostic Settings
A Better way to monitor the usage of basic authentication protocols is by sending all logs to a Log Analytics Workspace. You get a lot more history and a few built-in workbooks. If required, it’s also possible to configure alerts.
Although the Log Analytics Workspace will be free, an Azure Subscription is required to set this up. Also, Azure AD P1 is required to export your sign-in logs.
- Navigate to https://portal.azure.com and log on with a user that has sufficient permissions.
- Be sure to register Microsoft.Insights (sometimes it doesn’t happen automatically) by going to your subscription and clicking Resource Providers. Choose Microsoft.Insights and click Register.

- Create a new Log Analytics Workspace. The Pay-asyou-go pricing tier gives you 5GB for free.
- Navigate to Azure Active Directory > Diagnostic Settings. You’ll find the in the Monitor Section.
- Click +Add Diagnostic Setting.
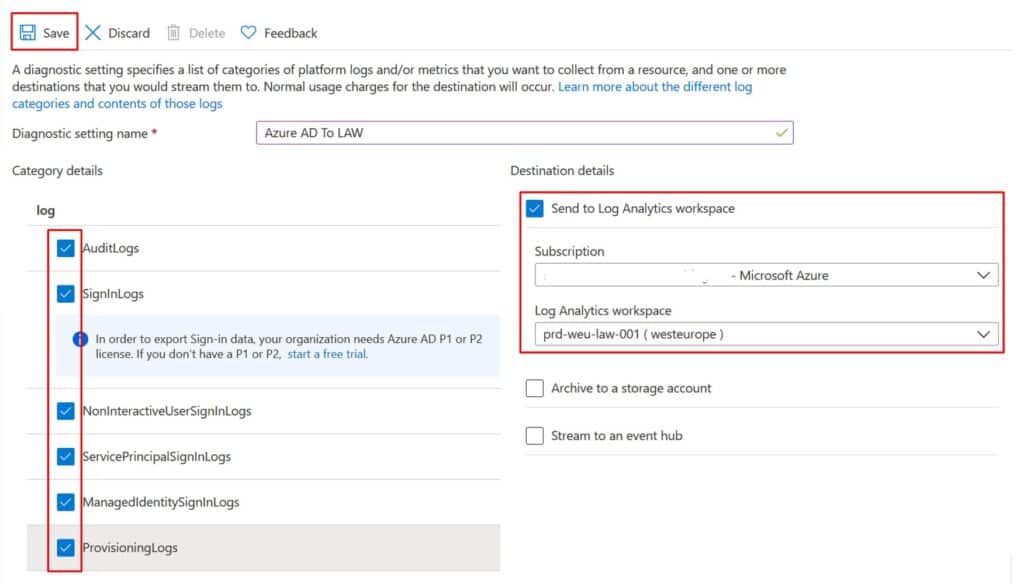
- Select all logs and click Send to Log Analytics workspace. Select your workspace and click Save.
- Click on Workbooks (also in the Monitoring section in Azure AD) and click Sign-in using Legacy Authentication. Keep in mind that it can take a while for your data to appear.
Enable Modern Authentication
Before blocking all legacy authentication protocols you need to make sure that your users can use the new way of authenticating. Modern authentication is enabled by default for every tenant created after August 1, 2017 but if you’re on an older tenant you need to enable modern authentication for Exchange Online and Skype for Business Online (if you haven’t migrated to Microsoft Teams already). You can’t enable modern authentication for a subset of users – the setting is tenant wide.
Exchange Online
Microsoft 365 Admin Center
You enable Modern Authentication in the Microsoft 365 Admin Center or with PowerShell.
- Navigate to https://portal.microsoft.com and log on with a Global Administrator.
- Click on Settings > Org Settings
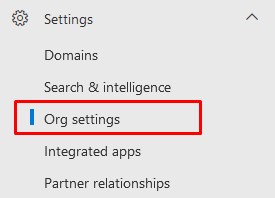
- Click on Modern Authentication and select Turn on modern authentication for Outlook 2013 for Windows and later (it must be selected, don’t deselect it).
PowerShell
It only requires one command to enable modern authentication with PowerShell.
- Connect to Exchange Online via PowerShell.
- After connecting, enter the command below.
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
You can check if Modern Authentication is enabled successfully by using the following command.
Get-OrganizationConfig | Format-Table Name,OAuth* -Auto
Skype for Business Online
Modern authentication for Skype for Business Online can only be enabled by using PowerShell.
- Download and install the Skype for Business Online PowerShell Module.
- Connect to Skype for Business Online.
- After connectiong, enter the command below.
Set-CsOAuthConfiguration -ClientAdalAuthOverride Allowed
You can check if Modern Authentication is enabled successfully by using the command below. The value should be Allowed.
Get-CsOAuthConfiguration | Format-Table ClientAdalAuthOverride
Block Legacy Authentication – before Microsoft does it for you
As stated before, Microsoft will start blocking Legacy Authentication in the second half of 2021. This doesn’t mean you should try blocking it before they do it. The most flexibel way to block legacy authentication is by using conditional access. Conditional access is a feature that’s included with all licenses that include Azure AD P1. If you don’t have these licenses your only option to block these protocols is by using the Microsoft 365 Admin Center or by enabling the Security Defaults. With both options, it’s not possible to exclude users.
Microsoft 365 Partner Center
These settings will block basic authentication policies in Exchange Online, but it’s not possible to exclude users.
- Navigate to https://portal.microsoft.com
- Click on Settings > Org settings

- Click on Modern Authentication and unselect all basic authentication protocols (or the ones you are ready for).
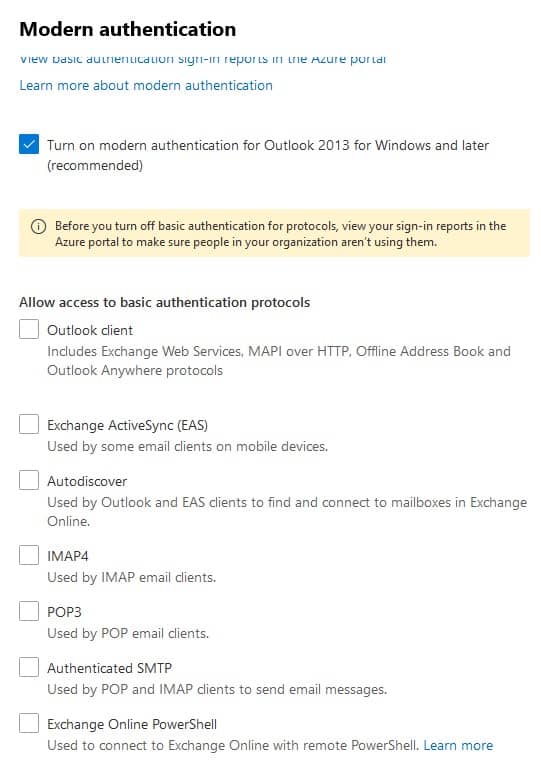
- Don’t forget to click Save.
Security Defaults
Enabling security defaults will enable other security features besides blocking legacy authentication – like enabling multi-factor authentication! Enabling this feature will have user impact.
By enabling security defaults you will enforce all security features below on all users – no exceptions. It’s not possible to enable security defaults AND disable the protocols via the Microsoft Admin Center. The reason is that security defaults are not using the Exchange Authentication Policies.
- Multi-factor authentication is enabled for every user. Users will have 14 days to complete the registration. Only the Microsoft Authenticator app is allowed (no phone calls or SMS). Users will be prompted for MFA ‘whenever necessary’.
- Multi-factor authentication is enabled for all administrator roles.
- All legacy authentication protocols are blocked.
After reviewing the impact above you can enable the security defaults by using the Azure Portal.
- Navigate to https://portal.azure.com end log on with a user that has sufficient permissions.
- Open the Azure Active Directory Blade and click Properties.
- Scroll to the bottom of the page and click Manage Security Defaults.
- Select Yes and click Save.
Conditional Access
The best way to block legacy authentication (if you need flexibility) is by using conditional access. An Azure AD P1 license is required for every user to be compliant.
- Navigate the https://portal.azure.com
- Open the Azure AD Conditional Access blade.
- Click on + New Policy to start.
- Enter a name that indicates the goal of the policy.
[BLOCK] – Legacy Authentication - Click Users and Groups and select All Users. Don’t try to exclude any users – except your breakglass account (if applicable).
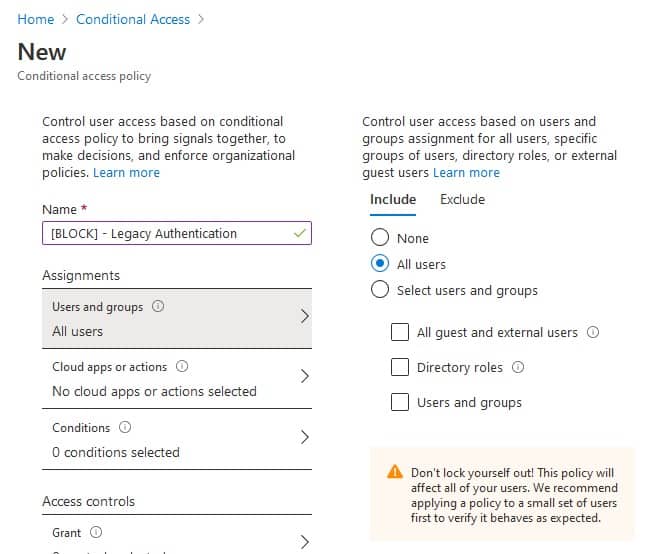
- Click Cloud Apps or actions and select All Cloud Apps.
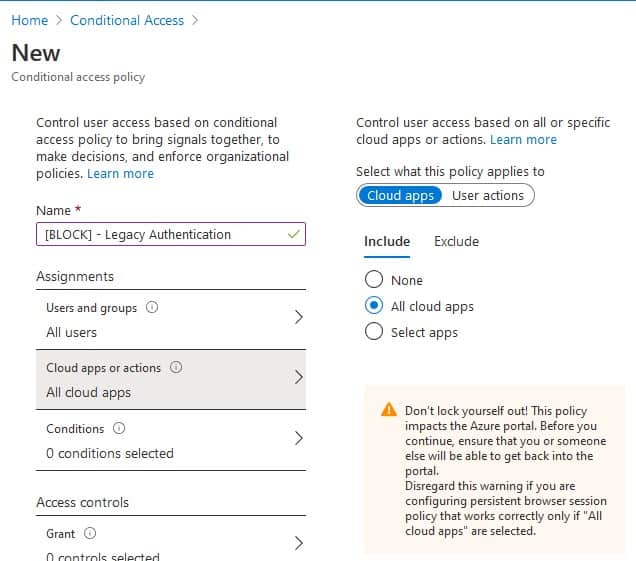
- Click on Conditions > Client Apps. Select Yes and only select the Legacy Clients.
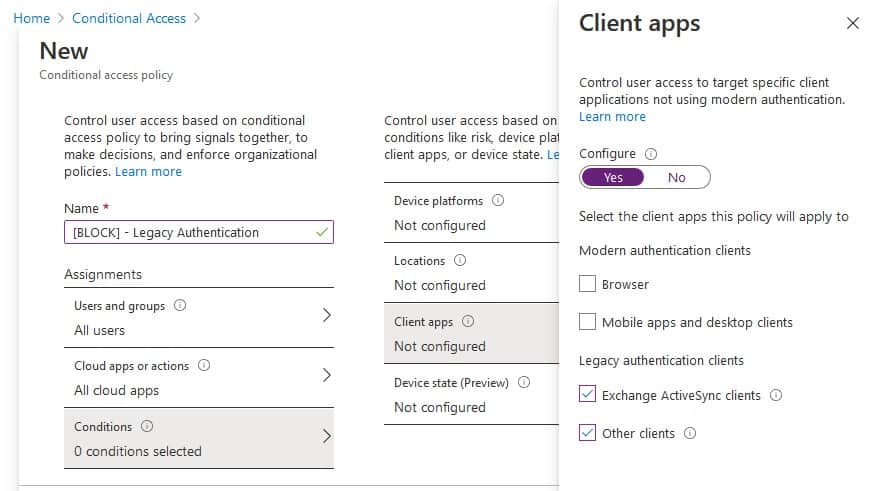
- Click Grant and select Block Access.
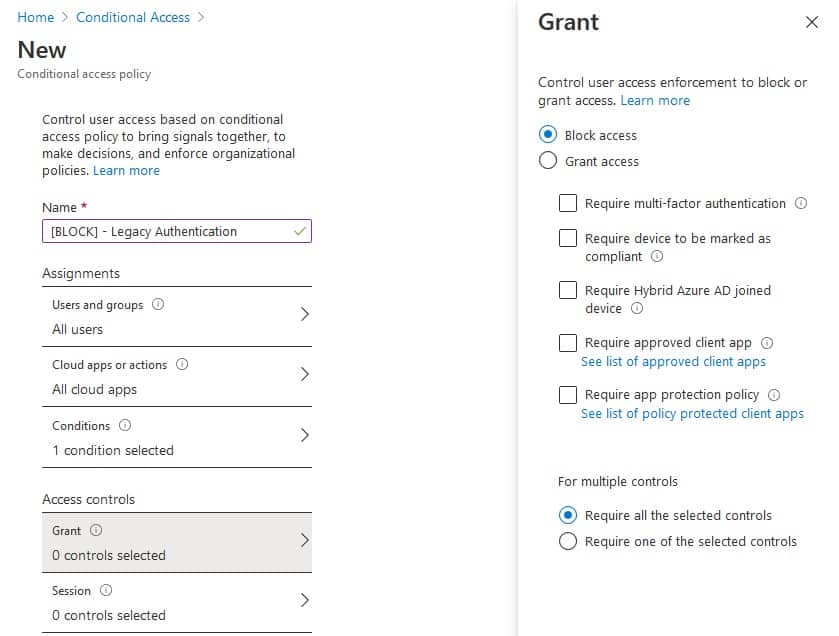
- If your not sure start by enabling the policy in report-only. Otherwise, select On.
Legacy Authentication in Exchange Online
Conditional access is aplied after the user signs in. This means that legacy authentication is blocked only after a correct password is received. A Brute force attack that uses legacy protocols (POP, IMAP, ..) will not be blocked by conditional access and and therefore your on-premises or Azure AD account lockout policies will apply. This can result in unwanted blocked accounts – even with smart lockouts enabled. The only way to fix this is by blocking legacy authentication in Exchange Online using PowerShell, or disable the protocols in the Microsoft 365 Admin Center (like explained above). If you need to exclude users, this is the only way to do it.
If you’ve enabled security defaults in your organization, Basic authentication is already disabled in Exchange Online. When using conditional access, you need to manually block legacy authentication using PowerShell.
- Connect to Exchange Online using PowerShell.
- Use the command below to block all legacy protocols.
New-AuthenticationPolicy -Name "Block Legacy Authentication" Set-OrganizationConfig -DefaultAuthenticationPolicy "Block Legacy Authentication"
By default the new authentication policy will block all basic authentication policies if you don’t specify any arguments. The command above will block all legacy protocols for all users. If you want to apply the policy to a subset of users (or a single user) you can use the command below. Be aware that policies applied to users take precedence to the default policy.
Set-User -Identity jente@azurescene.com -AuthenticationPolicy "Block Legacy Authentication"
[…] An update on Legacy Authentication […]
What happens to COTS application that relay on smtp example Sharepoint 2016 , or SQL server on prem that send mails, or any third party service that is vendor built and they dont update their modern authentication. ?
Some routers, switches, and other devices who work with no authentication or only basic authentication only. How to handle this scenario.
[…] An update on Legacy Authentication | Azure Scene […]