Legacy authentication refers to authentication request made by older Office clients (2010 and below) or other clients that use old protocols like IMAP, POP3 or SMTP. Legacy authentication is unsafe because you can’t enforce multi-factor authentication on them – that’s why enabling MFA for your users isn’t effective if you don’t block legacy protocols. Microsoft gave us some numbers to make this very clear.
- More than 99 percent of password spray attacks use legacy authentication protocols.
- More than 97 percent of credential stuffing attacks use legacy authentication.
- Azure AD accounts in organizations that have disabled legacy authentication experience 67 percent fewer compromises than those where legacy authentication is enabled.
This blog post is part of my Azure AD Best Practices post.
Update: Azure AD P1 is now included in Microsoft 365 Business (Premium)!
Legacy Authentication Protocols
The options below are considered legacy.
- Authenticated SMTP
- Exchange Online PowerShell
- Exchange Web Services
- IMAP
- MAPI over HTTP
- OAB (Offline Address Book)
- Outlook Anywhere
- Outlook Service
- POP3
- Reporting Web Services
- Other clients
Monitor Legacy Authentication Usage
Microsoft made it very easy to check if your organisation is using legacy authentication protocols by using the sign-in logs. Sign-in logs are now free for every Azure AD tenant, but without a license you can only go back 7 days. If you need more history you need Azure AD P1 or above.
- Navigate to https://portal.azure.com and log on with a user that has sufficient permissions.
Global Administrator, Security Administrator, Security Reader, Global Reader and Report Reader roles can access sign-in logs.
- Open the Azure Active Directory blade and click Sign-ins – you’ll find this under the Monitor section.
- Add a filter by clicking Add Filters and choose Client App. Click Apply.
- Select all Legacy Authentication Protocols.
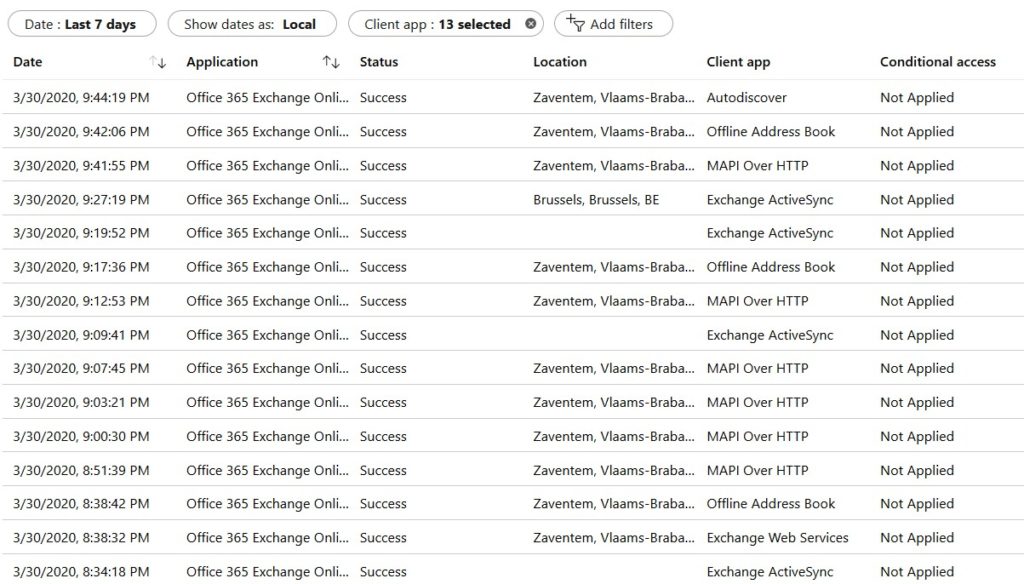
- Analyse all sign-ins or click Download to export a JSON/CSV.
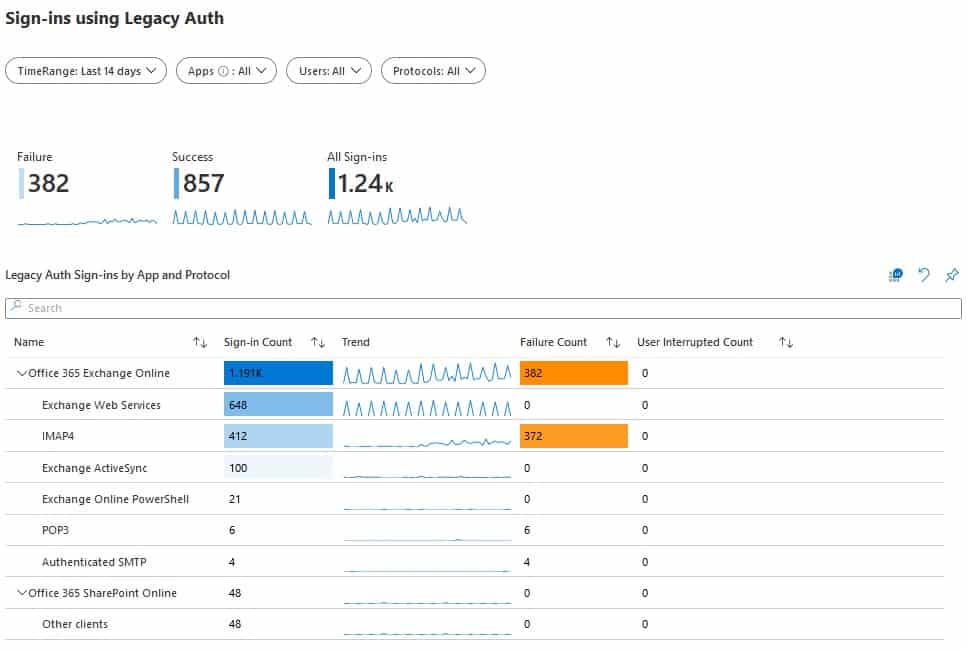
Another (and even easier) way of analysing legacy authentication usage is by using the built-workbook in Azure AD.
- Navigate to https://portal.azure.com and log on with a user that has sufficient permissions.
- Open the Azure Active Directory blade and click Workbooks. you’ll find this under the Monitor section.
- Open the Sign-ins using Legacy Authentication workbook.
Enable Modern Authentication
Before blocking all legacy authentication protocols you need to make sure that your users can use the new way of authenticating. Modern authentication is enabled by default for every tenant created after August 1, 2017 but if you’re on an older tenant you need to enable modern authentication for Exchange Online and Skype for Business Online (if you haven’t migrated to Microsoft Teams already). You can’t enable modern authentication for a subset of users – the setting is tenant wide.
Exchange Online
Microsoft 365 Admin Center
You enable modern authentication in the Microsoft 365 Admin Center or with PowerShell.
- Navigate to the Microsoft 365 Admin Center and log on with a global administrator.
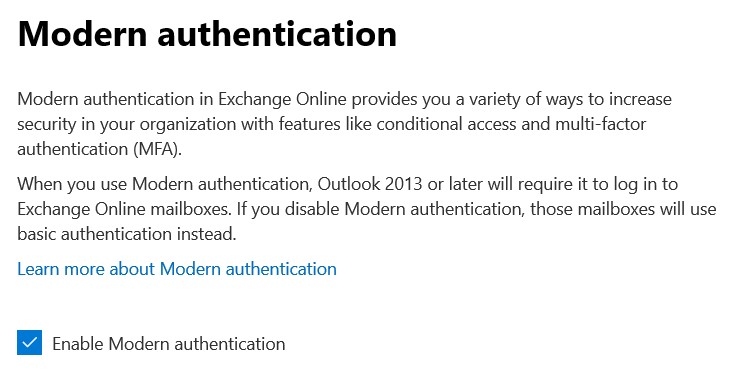
- Click Settings.
- Under the services tab you’ll find Modern authentication.
- Check Enable modern authentication to enable.
PowerShell
It only requires one command to enable modern authentication with PowerShell.
- Connecto to Exchange Online PowerShell.
- After connecting, enter the command below.
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
You can check if modern authentication is enabled successfully by using the following command.
Get-OrganizationConfig | Format-Table Name,OAuth* -Auto
Skype for Business Online
Modern authentication for Skype for Business Online can only be enabled by using PowerShell.
- Download and install the Skype for Business Online PowerShell Module.
- Connect to Skype for Business Online
- After connecting enter the command below.
Set-CsOAuthConfiguration -ClientAdalAuthOverride Allowed
You can check if modern authentication is enabled successfully by using the command below. The value should be Allowed.
Get-CsOAuthConfiguration | Format-Table ClientAdalAuthOverride
Block Legacy Authentication
The most flexibel way to block legacy authentication is by using conditional access. Conditional access is a feature that’s included with all licenses that include Azure AD P1. If you don’t have these licenses your only option to block these protocols is by enabling the security defaults.
Security Defaults
Enabling security defaults will enable other security features besides blocking legacy authentication! Enabling this feature will have user impact.
By enabling security defaults you will enforce all security features below on all users – no exceptions.
- Multi-factor authentication is enabled for every user. Users will have 14 days to complete the registration. Only the Microsoft Authenticator app is allowed (no phone calls or SMS). Users will be prompted for MFA ‘whenever necessary’.
- Multi-factor authentication is enabled for all administrator roles.
- All legacy authentication protocols are blocked.
After reviewing the impact above you can enable the security defaults by using the Azure Portal.
- Navigate to the Azure Portal and log on with a user that has sufficient permissions.
Global Administrator, Security Administrator or Conditional Access Administrator.
- Open the Azure Active Directory blade and click Properties.
- Scroll to the bottom of the page and click Manage Security Defaults.
- Select Yes and Save.
Conditional Access
The better and more flexible way of blocking legacy authentication is by using conditional access.
- Navigate to the Azure Portal and log on with a user that has sufficient permissions.
Global Administrator, Security Administrator, or Conditional Access Administrator.
- Open the Azure AD Conditional Access blade.
- Ignore all baseline policies. They are deprecated.
- Click New Policy to start.
- Enter a name that indicates the goal of the policy.
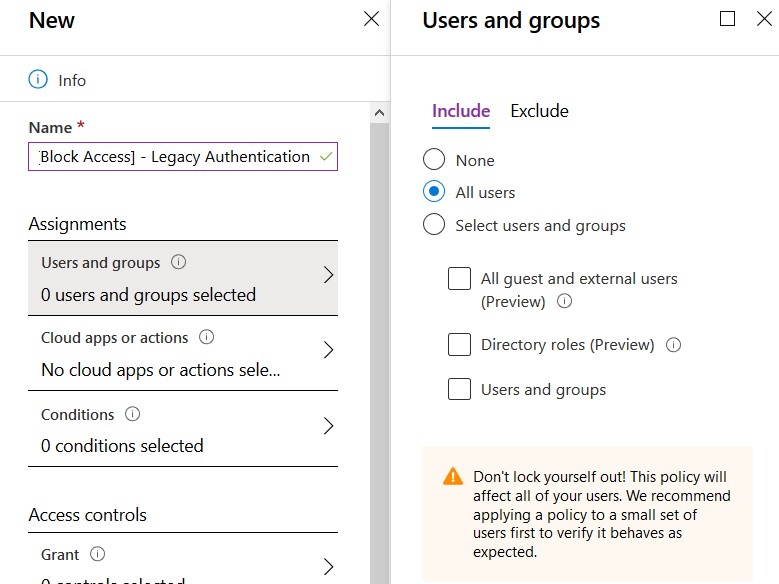
[Block Access] – Legacy Authentication - Click Users and groups and select All Users. If required you can exclude users or groups (I don’t recommend this). Don’t forget to click Done.
- Click Cloud apps or actions and select All cloud apps.
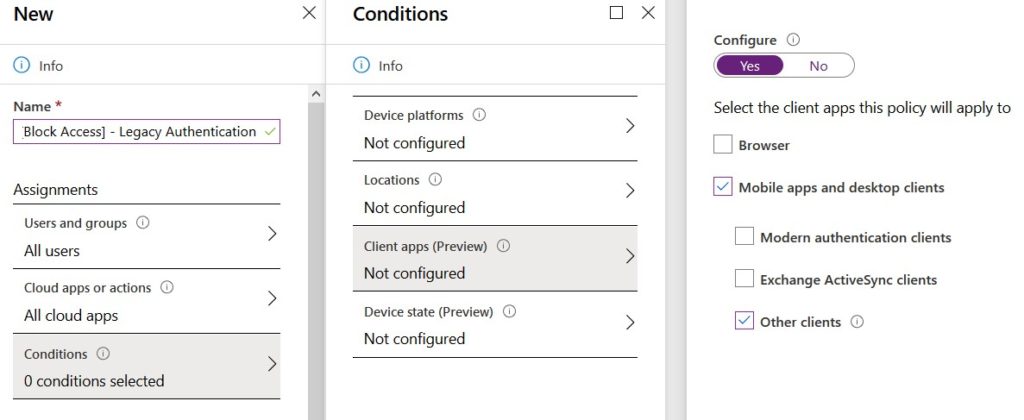
- Click Conditions followed by Client apps. Select Yes to configure and select Mobile apps and desktop clients and other clients.
- Click Grant and select Block access. You can ignore the multiple controls setting.
- Enable the policy by selecting report-only or On. I Suggest you start with report-only.
Legacy Authentication in Exchange Online
Conditional access is aplied after the user signs in. This means that legacy authentication is blocked only after a correct password is received. A Brute force attack that uses legacy protocols (POP, IMAP, ..) will not be blocked by conditional access and and therefore your on-premises or Azure AD account lockout policies will apply. This can result in unwanted blocked accounts – even with smart lockouts enabled. The only way to fix this is by blocking legacy authentication in Exchange Online.
If you’ve enabled security defaults in your organization, Basic authentication is already disabled in Exchange Online. When using conditional access, you need to manually block legacy authentication using PowerShell.
- Connect to Exchange Online using PowerShell.
- Use the command below to block all legacy protocols.
New-AuthenticationPolicy -Name "Block Legacy Authentication" Set-OrganizationConfig -DefaultAuthenticationPolicy "Block Legacy Authentication"
By default the new authentication policy will block all basic authentication policies if you don’t specify any arguments. The command above will block all legacy protocols for all users. If you want to apply the policy to a subset of users (or a single user) you can use the command below. Be aware that policies applied to users take precedence to the default policy.
Set-User -Identity jente@azurescene.com -AuthenticationPolicy "Block Legacy Authentication"
You’ve now successfully blocked all legacy authentication protocols. Don’t forget to enable multi-factor authentication tho!