Azure AD Identity Protection requires Azure AD P2 licenses. Azure AD Identity Protection is not included with Azure AD P1 or Microsoft 365 Business.
Azure AD Identity protection is a premium tool that analyses 6.5 trillion signals per day to identify and protect customers from threats. Identity protection has two types of risk where some are calculated offline and some in realtime.
This blog post is part of my Azure AD Best Practices post.
User risk
User risks are calculated offline by Microsoft’s internal and external threat intelligence sources. These sources include security researchers, law enforcement professionals, security teams at Microsoft and more. A user risk represents the probability that a user is compromised. User risk is always calculated offline.
Leaked credentials
The Microsoft leaked credentials service acquires credentials on the dark web, paste sites, password dumps and more. All these passwords are checked against the users’ current credentials to find a match.
Azure AD threat intelligence
The activity of the user is compared with the normal activity for the given user. Unusual activy or activity that is consistent with known attach patterns will be flagged.
Sign-in risk
A Sign-in risk is calculated offline or in realtime and represents the probablity that an authentication request isn’t legit. Unlike User risk, there are more detection types in place.
Do you see ‘additional risk detected‘ in your portal? This means that one of the risks below is detected. Additional risk detected is shown to customers without Azure AD P2 licenses.
Admin confirmed user compromised
When an admin has selected confirm user compromised in the risky user portal (or by using Microsoft Graph).
Atypical travel
Atypical travel is an offline detection type that identifies sign-ins originating from geographically distant locations. A machine learning algorithm takes the past behavior of the user into account to identify the risk. Impossible travel time will indicate that a different user is using the credentials to log on.
Atypical travel has a learning period of 14 days or 10 logins (whatever comes first) in which in learns the sign-in behavior of a new user. Because of this, false positives are being ignored (regulary locations in the organization, VPN’s, ..)
Anonymous IP Address
Anonymous is a realtime detection type that identifies sign-ins from IP addresses that are used by VPN services or anonymous browsers like Tor. These services are typically used by people with malicious intent.
Unfamiliar sign-in properties
Unfamiliar sign-in properties is a realtime detection type that compares sign-ins with the sign-in history of a user. The risk score is computed in real-time while logging on and looks at IP address, location, known/past IP addresses, IP carriers and browser sessions.
Unfamiliar sign-in properties has a dynamic learning period. A user will be in learning mode for a minimum duration of five days untill the algorith has enough information about the users behavior.
Malware linked IP address
Malware linked IP address is an offline detection type that will trigger when a sign-in from an IP address that is known to actively communicate with a bot server.
Malicious IP address
Malicious IP address is an offline detection type that indicates sign-in from an IP address that has a high logon failure rate because of invalid credentials.
Configure Azure AD Identity Protection
3 policies should be enabled to fully use the capabilities of Identity Protection. Keep in mind that there will be user impact.
MFA registration policy
The MFA registration policy will manage the roll-out of Azure Multi-Factor Authentication registration by configuring a Conditional Access policy to require MFA. Even if MFA is not enabled, MFA registration is required. Be sure to configure this policy when using Identity Protection because it will have impact on the policies below.
Enabling this policy will have impact on the users that are scoped in this policy. After enabling the policy users will be prompted to register for multi-factor authentication. Users will have 14 days to complete registration and are able to skip to prompts in this period. After 14 days they are forced to complete registration before they can sign in. If users already have registered for MFA they won’t see this prompt.
- Sign-in to your Azure Portal as global administrator.
- Seach for Azure AD Identity Protection
- Click on the MFA registration policy to start configuring.
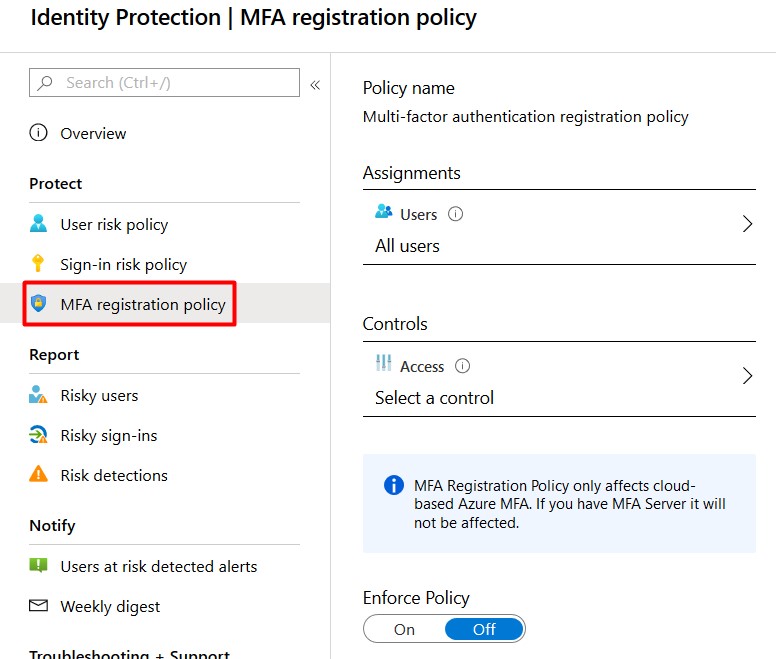
- Assign the policy to All Users. It possible to exclude users or groups if needed but I advise you don’t do this.
- Be sure to select Require Azure MFA registration under Controls.
- Enforce the policy and click Save.
User risk policy
Enabling this policy will have impact on the users that are flaged as risky. Use the Overview page to investigate the current situation.
When this policy is triggered the user will be required to use muti-factor authentication and change their password. Users who aren’t registered for MFA will be blocked from accessing the account. If a user is blocked, and admin is required to unblock the account.
- Click on the User risk policy to start configuring.
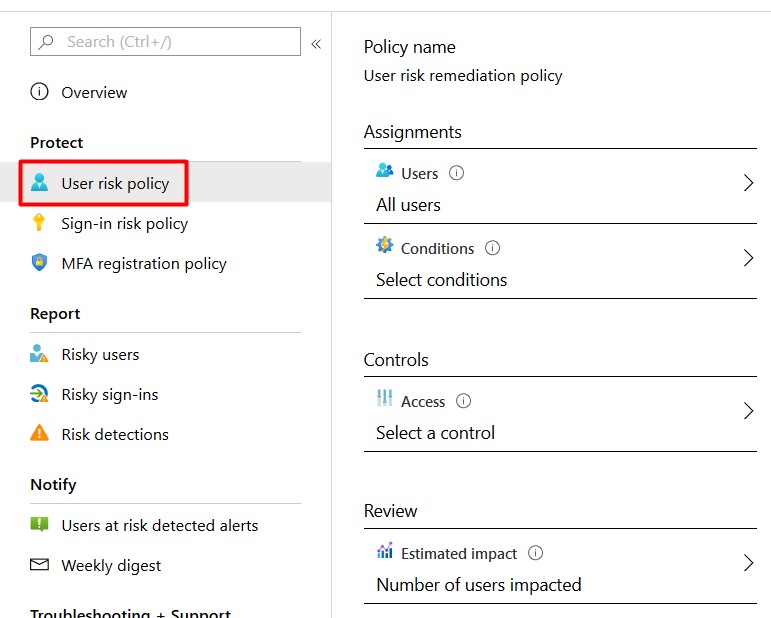
- Assign the policy to All Users.
- Click Conditions and select the approporiate user risk level. Microsoft’s recommendation is to set the user risk policy threshold to High. Depending on your environment i should try Medium and above (after investigating user impact).
- Click Controls and be sure to check Allow Access, Require password change.
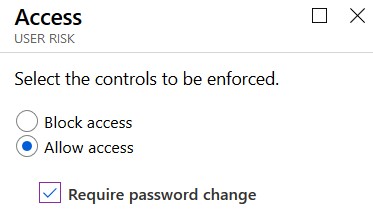
- Optional: Review the impact on your environment. You should do this before configurin the policy by using the Overview page.
- Enforce the policy and click Save.
Sign-in risk policy
Enabling this policy will have impact on the users that are flaged as risky. Use the Overview page to investigate the current situation.
When this policy is triggered the user will be required to use muti-factor authentication before accessing the account. Users who aren’t registered for MFA will be blocked. If a user is blocked, and admin is required to unblock the account.
- Click on the Sign-in risk policy to start configuring.
- Assign the policy to All Users.
- Click Conditions and select the approporiate user risk level. Microsoft’s recommendation is to set the sign-in risk policy threshold to Medium and above.
- Click Controls and select Require multi-factor authentication.
- Optional: Review the impact on your environment. You should do this before configurin the policy by using the Overview page.
- Enforce the policy and click Save.
Notifications
it’s advisable to review your risky users and sign-ins every week. Depending on your policy low or medium risky users aren’t required to act, but there could be something going on. Be sure to enable notifications/email alerting on an approporiate risk level.
- Click on Users at risk detected alerts.
- Select the approporiate risk level (Medium is a perfect choice).
- Select your recipients and click save.
Weekly email digests can help you to review the risk every week so be sure to enable this as well!
Guest Users
Configuring the policies above will have impact on all Guest users in your tenant. Have a look at my blog post explaining this.
That’s it! You’re done configuring Azure AD Identity Protection and you tenant is more secure than before. Don’t forget to review the risky users and sign-ins weekly. Got questions or tips? Just leave a comment!
Hi,
What are the best approaches to tune unfamiliar sign-in and atypical travel as these are very noisy at the moment. Our environment is in the education sector and currently doesn’t seen to cope very well AAD identity protection.
Hello! I’m afraid that’s not possible. This is a feature, completely controlled by Microsoft.
True, but I think you can add IPs to Named Locations CAPs, and this will lower the risky sign-in detection and false positives.
You can label trusted IP address ranges in your organization with named locations. Azure AD uses named locations to:
-Detect false positives in risk detections. Signing in from a trusted location lowers a user’s sign-in risk.
https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/quickstart-configure-named-locations