A Few weeks ago I encountered a problem with a guest users that couldn’t login on my environment. After some troubleshooting, I noticed that the guest user needed to change his password for some kind of reason but I already checked my User Risk Policy report in the Azure AD Identity Protection blade. What was going on?
When reviewing the risky users in my tenant (Azure AD Identity Protectio > Report > Risky Users) I couldn’t see a single risky user. That’s when I started to look deeper and came across some limitations (perfectly documented on docs.com – my bad).
The user risk for B2B collaboration users is evaluated at the home directory of the guest user. The real-time sign-in risk for these users is evaluated at the resource directory when they try to access the resource. With this in mind, the following limitations will occur.
- Guest users do not appear in the risky users report. When a guest user is risky, only the administrator of their home directory can see this.
- You cannot dismiss or remediate a risky guest user user in your directory. This means that you cannot fix this problem yourself.
How to fix this?
To get your guest user back in action he/she needs to reset his/her password (according to your Identity Protection policies). If the users doesn’t want to do this you need to contact the administrator of the users’ home directory to reset the risk status.
To prevent this from happening in the future it’s possible to exclude all guest users from your identity protection policies by using a dynamic Azure AD Group.
- https://portal.azure.com
- Azure Active Directory > Groups > New Group
- Create a Security group with Dynamic User

- Add (user.userType -eq “Guest”) as dynamic rule to target all guest users.
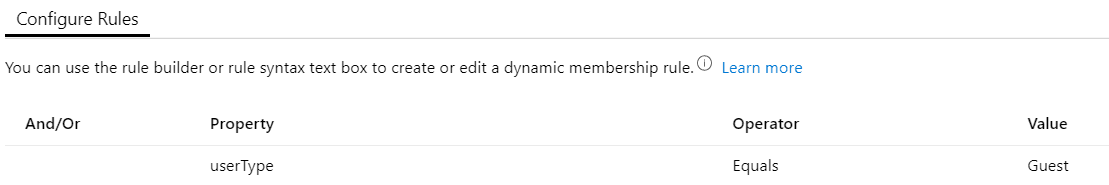
- Add your new group to the exclude list of your Identity Protection policies.
A Risky user stays a risky user, no matter what. My advice is to contact the administrator of the other directory to make sure you don’t give a risky user access to your resources.
Still not enabled Azure AD Identity Protection? Have a look at my blogpost on how to do this.
